React's React2Shell Hack: When Your UI Library Gets a Backdoor
React's React2Shell Hack: When Your UI Library Gets a Backdoor
Picture this: You're sipping coffee, deploying your shiny Next.js app to prod, thinking, "Man, React makes frontend life easy." Then boom – hackers are SSH-ing into your server via a malicious HTTP request. No auth, no fuss, just pure, unadulterated RCE chaos. Welcome to the React2Shell saga, where a "server component" turned into a backdoor for the ages.
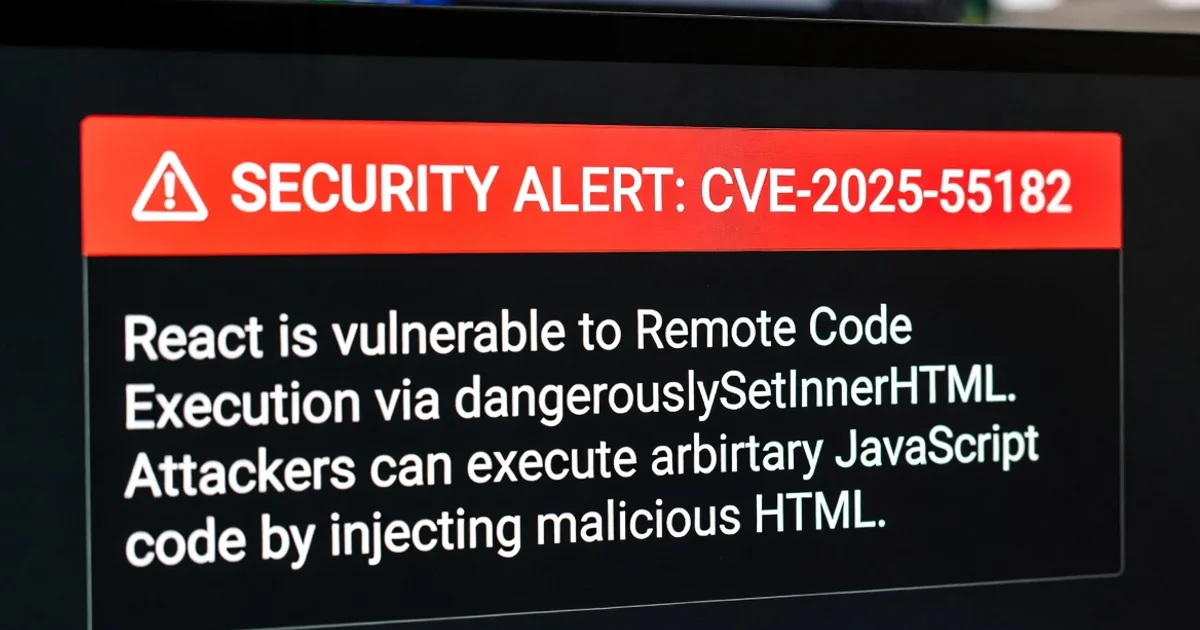
On December 3, 2025, the React team dropped a bomb: CVE-2025-55182, a CVSS 10.0 critical vuln in React Server Components (RSC). And like any good internet drama, Chinese APT groups were exploiting it within hours. If your app uses React 19 on the server side, congrats – you might've just hosted a free hacker convention.
What Actually Happened? (The Technical Bit, Minus the Eye Rolls)
At its core, this was an old-school deserialization blunder dressed up in modern RSC finery. React's Flight protocol – the magic that shuttles server-rendered components to the client – has a dirty secret: it trusts incoming payloads a bit too much.
Here's the oversimplified autopsy (because nobody wants a 10-page diff of the react-server package):
- The Setup: RSC lets you write server-only components that get serialized and sent over the wire. Cool for perf, right? But the deserialization on the server side? Yeah, that's where things get spicy.
- The Bug: In versions 19.0 through 19.2.0 of
react-server(and friends likereact-dom/server), the Flight protocol chokes on insecure deserialization. Attackers craft a payload with nested objects or funky prototypes, tricking Node.js into eval-ing arbitrary code. - The Trigger: One unauthenticated POST request to an RSC endpoint (think
/api/rscor whatever your Next.js App Router exposes). Headers likenext-actionorrsc-action-idget hijacked, and poof – shell access. - The Cascade: Next.js (CVE-2025-66478, now merged into the main one) inherits the flaw because it bundles vulnerable React. Other victims? Vite RSC plugin, RedwoodJS, even Waku. If it touches RSC, it's toast.
- The Exploitation: PoCs hit GitHub same day. By Dec 4, Earth Lamia and Jackpot Panda were probing AWS honeypots. Huntress spotted "PeerBlight," a Go-based backdoor dropping ELF binaries for persistence. GreyNoise clocked scans spiking 1,000% overnight.
Result? Over 12 million sites exposed, per HackerOne. Wiz says 39% of cloud envs are vulnerable. Palo Alto's Unit 42: 968,000+ servers ripe for the picking. And yes, your grandma's blog on Vercel? Probably fine if it's static, but server-side? Time to sweat.
Moral: Deserialization is the gift that keeps on giving... headaches. (Pro tip: Never trust data from the internet, especially when it's promising "seamless server rendering.")
Who Got Hit? (The Casualty List)
React powers 40% of dev surveys, Next.js 20%. That's everyone:
- Next.js Apps: App Router users? Slammed. Static exports? Dodged a bullet.
- Enterprise Giants: Think any Fortune 500 with a React SPA. Early reports: CMS platforms on Node.js went dark.
- Cloud Hosts: AWS EC2, containers – if you're self-managing, you're exposed. Managed services? AWS says they're safe.
- APT Playground: Chinese groups used it for recon on critical infra – nuclear fuel suppliers, rare earth miners. Because why hack a bank when you can disrupt the periodic table?
- Indie Devs: That side project on Render or Fly.io? If unpatched, it's now a botnet recruit.
Stock impact? Meta (React's overlords) dipped 2%, but npm downloads for patched versions skyrocketed 500%. Silver lining: Security researchers got a bounty payday.
The Humour in the Chaos
My favorite X post amid the panic:
“React Server Components: Because who doesn't want their UI library to double as a rootkit? #React2Shell – now with 100% more unsolicited shells.”
— @some_sre_jester, Dec 3, 2025
Or the gem:
“Upgrading React like: 'This patch fixes RCE.' Me: 'Sweet, no more free VPNs for randos.'”
We've all been there. You npm install the latest hype feature, grep for "secure," see green tests... and suddenly your logs are full of whoami from Beijing. Classic Monday.
Lessons for Us Mere Mortals (DevOps Takeaways)
Look, if you're deploying React/Next.js, treat this like that time you forgot to rotate your API keys – embarrassing, but fixable. Here's your action plan:
- Patch Immediately: Upgrade to React 19.2.1+, Next.js 16.0.10+ (or whatever the fixed canary is). Run
npm update react react-dom react-serverand test like your job depends on it (it does). - Audit Your Stack: Use tools like Prisma Cloud or OX Security to scan for vulnerable deps. SBOMs aren't just buzzwords – generate one and grep for "19.0".
- Runtime Protections: WAF rules (AWS Managed Rules v1.24+), input validation on RSC endpoints. Block funky headers like
$ACTION_REF_0. - Monitoring Overkill: Prometheus for app metrics, Datadog for vuln alerts. Watch for IOCs: Weird POSTs to
/rsc, ELF drops (SHA256: 0f0f9c339fcc...). - CI/CD Lockdown: Fail builds on high-severity CVEs. Add deserialization checks in your linters – because "eval(userInput)" is never the answer.
- Incident Response: If compromised, nuke from orbit. AWS Support for forensics; Huntress for backdoor hunts.
- Future-Proof: Embrace zero-trust for your deps. Tools like Dependabot on steroids. And maybe... diversify beyond one framework? (Gasp!)
Bonus: If you're on Kubernetes (like my last Node.js guide), add those liveness probes to catch exploited pods early.
Final Thought
React2Shell is a stark reminder: Even the shiniest tools rust if you skip the security polish. In a world where half the web runs on one library, one bad deserial is a global whoopsie. But hey, patches exist, and hackers hate boring, updated code.
Stay vigilant, keep your package.json lean, and maybe pray a quick one for safe deploys. (Christianity tag incoming?)
Until next time – may your components render fast and your shells stay local.
P.S. React's postmortem is live on their blog. I'll link it when I stop laughing. 😏
UPDATE: Official React advisory – https://react.dev/blog/2025/12/03/critical-security-vulnerability-in-react-server-components
// RELATED_ARCHIVES
> Dec 2025 · 5 min read
React's RCE Wake-Up Call - Patch Before Hackers Say 'Hello World'
CVE-2025-55182 hits React Server Components hard with unauthenticated RCE. A quick dive into the deserialization drama, who's affected, and how to fix it without pulling your hair out.

> Dec 2025 · 5 min read
AWS's New AI Coders: Will They Finally Fix My Deployments?
AWS just dropped AI agents that can write, debug, and deploy code like a caffeinated intern. DevOps pros rejoice (or panic)

> Nov 2025 · 7 min read
The Cloud Is Just Someone Else’s Computer – Time to Go Local-First!
What if your app worked perfectly offline, synced magically, and you actually owned the data? Spoiler: it’s not sci-fi anymore.